INFORMATION SECURITY PENETRATION TEST

General introduction according to NIST
An information security assessment is the process of determining how effectively an entity being assessed (e.g., host, system, network, procedure, person—known as the assessment object) meets specific security objectives. Three types of assessment methods can be used to accomplish this—testing, examination, and interviewing. Testing is the process of exercising one or more assessment objects under specified conditions to compare actual and expected behaviors. Examination is the process of checking, inspecting, reviewing, observing, studying, or analyzing one or more assessment objects to facilitate understanding, achieve clarification, or obtain evidence. Interviewing is the process of conducting discussions with individuals or groups within an organization to facilitate understanding, achieve clarification, or identify the location of evidence. Assessment results are used to support the determination of security control effectiveness over time.
The importance of information system security testing and assessment
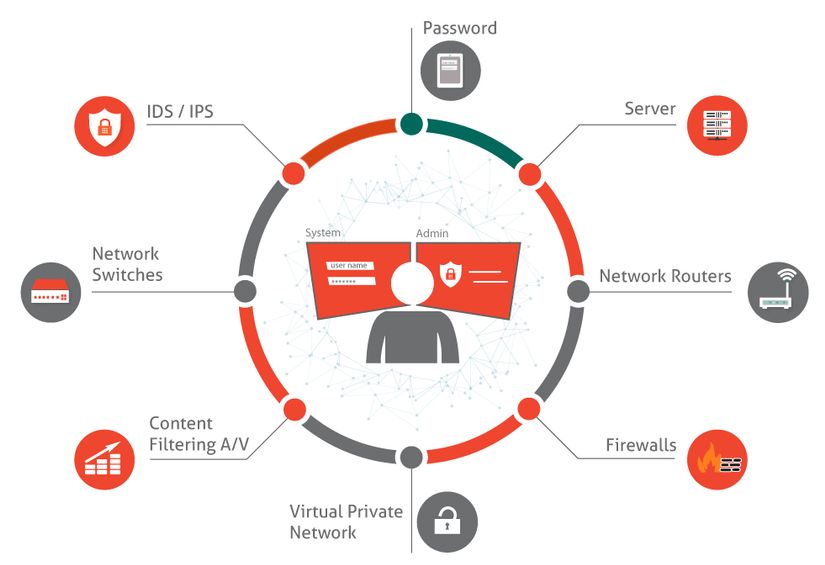
IT systems always have security weaknesses that hackers can exploit. Therefore, organizations need to be one step ahead of hackers, namely to find weaknesses in their IT systems and fix them before they are actually attacked by hackers.
However, the periodic assessment of an organization’s IT system is very complicated, and requires a high degree of objectivity, so organizations have turned to the use of Information Security Assessment and Testing Services from out-sources
Penetration Testing service, also known as Pentest for short, is a form of testing whether a customer’s IT system can be hacked or not, by acting as a hacker and simulating the Test attack on customer’s system. The main goals of the Pentest service include:
- Identify security weaknesses in the system.
- Provide recommendations and remedial methods for weaknesses found during pentesting.
- Check the organization’s information security policies.
- Check and evaluate users’ awareness when a cyber attack occurs on the organization.
Typically, information on security vulnerabilities identified and exploited through the pentest process will be aggregated and made available to organizations to assist organizations in planning strategies and priorities in increasing enhance security for the IT system of the organization.